VirusTotal 6/56
So I wanted a malspam honeypot. However, I was told that you would need to scatter your bait emails around websites, in order for spammers to scrape them up, to eventually receive spam. I thought about a way to jumpstart such a malspam honeypot to skip all email seeding and baiting but instead jump right to the receiving spam part.
The idea is to register a domain that was previously used by an email provider and turn it into a spam collector by collecting all the emails send to that domain.
tl;dr: You do receive immediate spam by turning an ex-email provider domain into a spam honeypot. However the amount of spam is only moderate and could be attained by spreading emails as well.
Get a list of email provider domains:
wget https://gist.githubusercontent.com/tbrianjones/5992856/raw/93213efb652749e226e69884d6c048e595c1280a/free_email_provider_domains.txtCheck domains not having a SOA DNS record:
cat free_email_provider_domains.txt |
while read domain; do
if [[ -z "$(dig soa $domain +short)" ]]; then
echo $domain;
fi;
done > free_email_provider_domains_without_soa.txtCheck which of these domains are registered:
cat free_email_provider_domains_without_soa.txt |
while read domain; do
echo -n "$domain: ";
whois $domain | grep -v "^$" | head -n 1;
done > free_email_provider_domains_whois_head.txtIf this says “No match for” the domain is not registered.
Check whether a domain has been widely used via https://www.google.com/search?q="@emaildomain.tld". You want something with at least a couple of thousand hits.
Optionally you can check via the Internet Archives Wayback Machine what was hosted on the domain via https://web.archive.org/web/*/http://emaildomain.tld. What you want to look for is the front end of a freemail provider. Ideally still active in the last couple of years.
If you found a suitable email domain that was wide spread and maybe still in use in the last years register it.
| Domain | Google results | Price | comment |
|---|---|---|---|
| id-base.com | 3.180 | €7.97/yr | I picked this one. |
| spacetowns.com | 1.390 | €953.49 | Too expensive. |
| kube93mail.com | 2.470 | €7.97/yr | |
| 1webhighway.com | 444 | €7.97/yr | |
| close2you.net | 358 | €11.65/yr | |
| fxsmails.com | 319 | €7.97/yr | |
| kapoorweb.com | 241 | €7.97/yr | |
| ifoward.com | 218 | €7.97/yr | |
| trashmail.de | 5.290 | NOT AVAILABLE | Only added for comparison. |
As you can see here my choice id-base.com has almost as many Google hits as a popular German disposable mail provider trashmail.de. Granted some of these hits included search results for telephones called “ID Base” or something, but registering that domain still seemed like a good choice.
I use a very cheap VPS hoster at $20/yr.
I use Cloudflare.
We configure Postfix to accept mails to all domains and all email addresses. This way we catch also (mal-)spam that was tried to be send via our “open relay”. (NOTE: We don’t run a open relay, however because we accept email to external domains from outside this looks like an open relay. Mail is never actually send from the server, though.)
/etc/postfix/vhosts:
/.*/ OK/etc/postfix/vmaps:
/.*/ id-base.com/spamtrap/The rest is configured like a normal mail transfer agent, however, some anti-spam measures have been loosened. Depending on what kind of spam you are after you may lower these even more.
/etc/postfix/main.cf:
smtpd_banner = $myhostname ESMTP
biff = no
myhostname = spamtrap.id-base.com
myorigin = $myhostname
mydestination = localhost, localhost.localdomain
relayhost =
mynetworks = 127.0.0.0/8
mailbox_size_limit = 0
home_mailbox = Maildir/
virtual_mailbox_domains = regexp:/etc/postfix/vhosts
virtual_mailbox_base = /home/vmail
virtual_mailbox_maps = regexp:/etc/postfix/vmaps
[...]
Because we registered a domain previously used by a legitimate mail provider, or at least a fun/throwaway mail provider, we do not get purely spam. We also get a lot of legitimate email that people signed up for.
However, during writing just the above paragraphs I already received:
Content-Type: application/octet-stream; name="New Order For July_pdf.img"… let’s quickly investigate our first possible malware sample already received during finishing setting the honeypot up!
$ sha1sum malware.img
5a017c21011cee78d9802f8b94f1ad7edb113206 malware.img
$ md5sum malware.img
24e6fc4b3579b1c3e57d99c37a14e651 malware.img
$ file malware.img
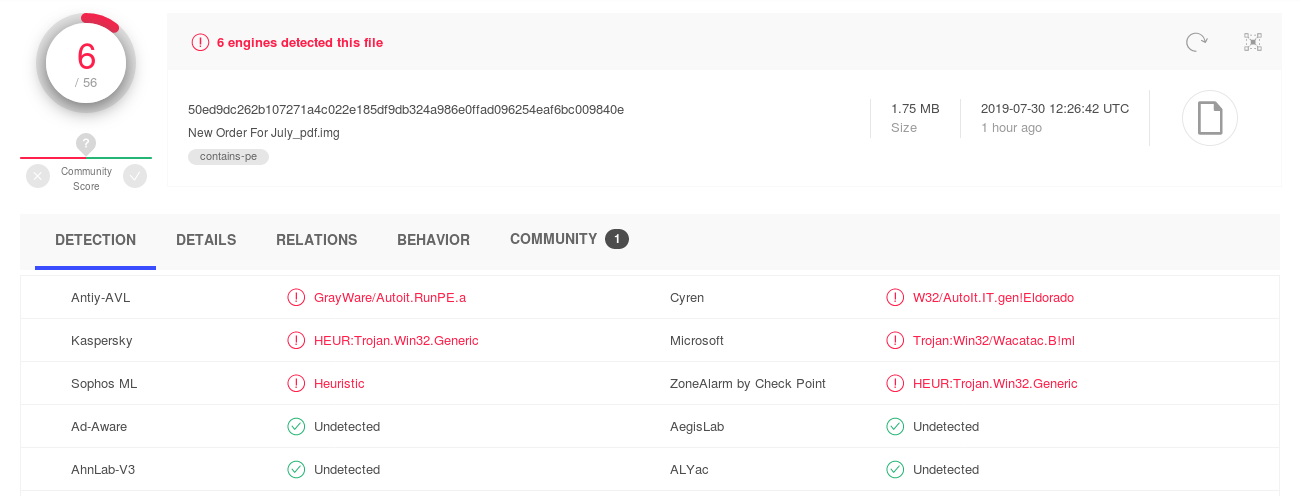
malware.img: # UDF filesystem data (version 1.5) 'DESKTOP'According to VirusTotal this is a malicous file with 6 of 56 AV engines recognizing it:

VirusTotal 6/56
We have received it 1h after the first submission to VirusTotal.
Looking inside the UDF filesystem we find an PE file:
$ mkdir malware
$ sudo mount -t udf malware.img malware
[sudo] password for user:
mount: /dev/loop0 is write-protected, mounting read-only
$ ls
New Order For July_pdf.exe
$ file New\ Order\ For\ July_pdf.exe
New Order For July_pdf.exe: PE32 executable (GUI) Intel 80386, for MS Windows
$ sha1sum New\ Order\ For\ July_pdf.exe
d035048349116a77cee226497707e31d7deb6745 New Order For July_pdf.exe
$ md5sum New\ Order\ For\ July_pdf.exe
d699957fdd5cd6127709f081216c4616 New Order For July_pdf.exeThis file has not been uploaded to VirusTotal yet. This means our spamtrap is a success. We just caught a potentially malicious binary that has not been submitted to VT before.
All this with just around 1h of time invested and a yearly cost of just 27.97 €!
The file itself was deemed malicious by 22 of 67 AV engines:
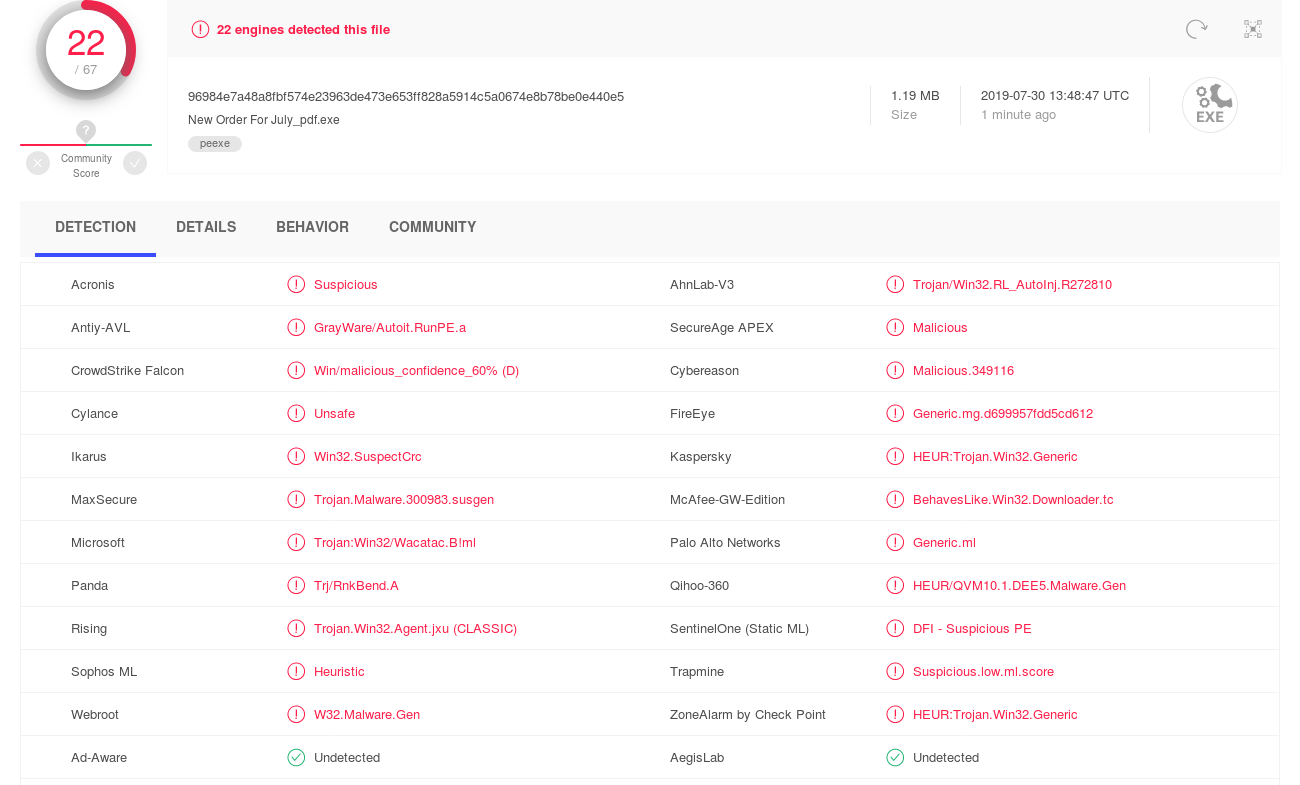
VirusTotal 22/67
You can get the sample here:
(Eventually, if I figure out some problems (see 7. The future) I may share the full stream of raw emails.)
Again, I have not yet spread any emails for this honeypot at all! And we already get malware sample! I quiet like that.
I initially intended to share the raw email stream for download with the community.
However, due to my jumpstarting tactic of registering a previous mail provider domain I’m faced with the following problems:
The domain holds 91 breached accounts according to ’;–have i been pwned?:
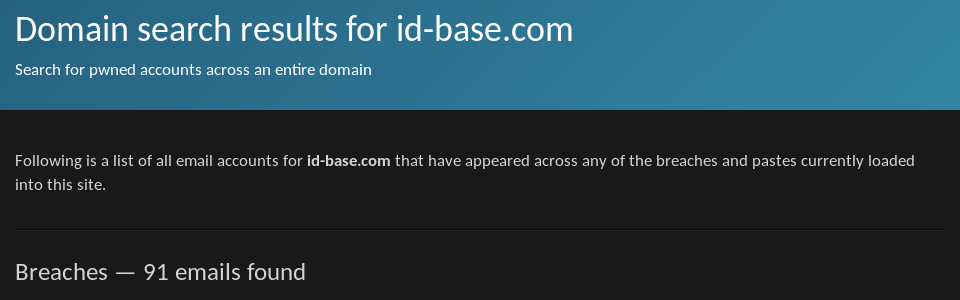
91 breached accounts on id-base.com according to ’;–have i been pwned?
So I can’t continue my initial plan to just put the webroot of http://download-spam.id-base.com to Maildir, as I’m not sure about the legal or social implications. I need to analyze the stream of emails for longer time to figure out how legit some of these emails have been used and then unsubscribe any services from these emails or something.
What I do want to do:
Authentication-Results: headers for DKIM and SPF to each email on receive (but not reject emails that fail them),root@localhost to a separate mailbox; discard password reset emails, etc. (so I can share the raw email stream without legal troubles); add URL and attachment extractors.While registering a domain previously used by a mail provider does help to shorten the initial gap to getting spam and malspam samples, it does only give a small advantage to baiting new emails from a virgin domain. For example, after around 6 hours the spamtrap at id-base.com has “only” received 50 emails. That is quiet nice for just 7.97 € spend on the domain, but can definitively be increased by feeding some mail addresses to spam scrapers.
However, what is probably unique about registering an old domain from a mail providers is the fact that people used these emails to register legitimate accounts, with 91 appearing in breached data. Now this fact could add quality to the malspam received by the emails on the domain overall as these are private email addresses that were not scraped from websites.
The solution is obviously extensible by adding more ex-email provider domains. However, that approach is limited as even completely broke mail providers can afford to pay 8 € for several years in an attempt to sell a popular domain for a higher price. So the domains that can be obtained via this method are old and thus often have not accepted any email for an extended period of time probably removing them from various lists already. But the approach can be taken for ex-company emails as well.
Which brings me to my original Tweet about this topic on the legality of getting ex-something domains and reading and potentially sharing all emails received:
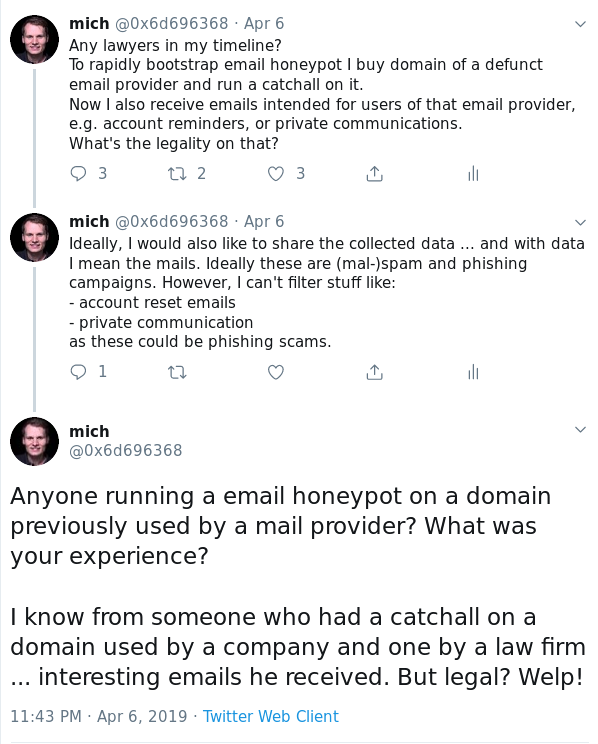
Tweet: “Any lawyers in my timeline? …”
Does anyone know? HALP!